What is a 🐬 Dolphin attack?
Has MarineLand become the theatre of atrocities?
Was Flipper a mass murderer?
Let’s find out today in this NorthSec challenge.
Science
A Dolphin attack is a term that has been given to the method of accessing a smartphone without the users’ consent by executing ultrasonic commands.
A study conducted at Zhejiang University in China has shown that such speech recognition systems are vulnerable to hidden commands that the researchers are calling “Dolphin Attacks”.
How do you hide a voice command? Make it ultrasonic.
Humans hear sounds between 20Hz and 20kHz. If you record a phrase, and shift it above 20kHz, then play it back, you can’t hear it, but dogs, bats, dolphins and, unfortunately, phone and computer microphones can.
Are 🐬 gonna’ take over the world?
Not in the near future, however “Dolphin Attacks” can be used to:
- Open malicious websites, which can launch a drive-by-download attack or exploit a device with 0-day vulnerabilities.
- Spy on users by initiating outgoing video/phone calls, therefore getting access to video or sound of the devices surroundings.
- Inject fake information by sending fake text messages and emails, online posts, calendar events, etc.
- Deny service, by turning on airplane mode, disconnecting all wireless communications.
- Conceal attacks by dimming the targeted device’s screen and lowering its speaker volume.
The challenge
In one of the challenges, you get access to this audio:
Thankfully we had heard about the dolphin attack vector (and the obvious name of the challenge), we decided to find
out if there was any hidden message in the audio.
The Audio opened in audacity reveals nothing on first hand:
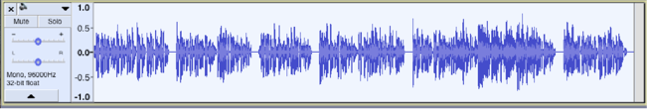
Unfortunately we did not succeed in attacking ourselves (I guess Apple had patched this flow on their side at the date of the competition). So after some looking around, we found how to get the message by demodulating the signal in amplitude using a nyquist prompt in Audacity:
;version 4
(setf cf 37000) ; the carrier frequency
(let ((demod (mult *track* (hzosc cf))))
(lowpass8 demod 10000))
Basically we filter everything under the high frequency and bring to audible level the hidden attack audio:
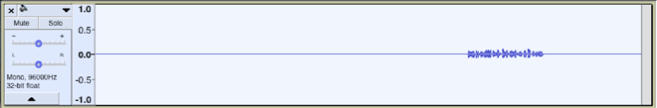
If you play the audio you should hear:
“hey siri go to tinyurl.com/56463452321”
Which bring you to this image where the flag The see weed brownies is written in plain text:

If you are wondering, to the disappointment of our teammates, no brownies were distributed during the event; Just half a truck of pizza 🍕 and a mountain of bagels 🥯.
See you next time Space Dolphin!